Process management is an integral part of any modern-day operating system. The OS must allocate resources to processes, enable processes to share and exchange information, protect the resources of each process from other processes and enable synchronization among processes. To meet these requirements, the OS must maintain a data structure for each process, which describes the state and resource ownership of that process, and which enables the OS to exert control over each process.
From the process management point of view, the Linux kernel is a preemptive multitasking operating system. As a multitasking OS, it allows multiple processes to share processors (CPUs) and other system resources. Each CPU executes a single task at a time. However, multitasking allows each processor to switch between tasks that are being executed without having to wait for each task to finish. For that, the kernel can, at any time, temporarily interrupt a task being carried out by the processor, and replace it by another task that can be new or a previously suspended one. The operation involving the swapping of the running task is called context switch.
💾 History: Till 2.6.39, kernel mode has only one thread protected by big kernel lock.
Processes
Process is a running user space program. Kernel starts the first process /sbin/init in function run_init_process idusing kernel_execve id. Processes occupy system resources, like memory, CPU time. System calls sys_fork id and sys_execve id are used to create new processes from user space. The process exit with an sys_exit id system call.
Linux inherits from Unix its basic process management system calls (⚲ API ↪ ⚙️ implementations):
man 2 fork ↪ kernel_clone id or _do_fork id creates a new process by duplicating the process invoking it.
man 2 _exit ↪ do_exit id terminates the calling process "immediately". Any open file descriptors belonging to the process are closed.
man 2 wait ↪ kernel_waitid id suspends the execution of the calling process until one of its children processes terminates.
man 2 execve ↪ do_execve id runs an executable file in the context of current process, replacing the previous executable. This system call is used by family of functions of libc man 3 exec
Linux enhances the traditional Unix process API with its own system calls man 2 clone. Clone creates a child process that may share parts of its execution context with the parent. It is often used to implement threads (though programmers will typically use a higher-level interface such as man 7 pthreads, implemented on top of clone).
📚 References
- unistd.h
- sys/types.h
- sys/wait.h
- fork (system call)
- exit (system call)
- wait (system call)
- exec (system call)
Inter-process communication
Inter-process communication (IPC) refers specifically to the mechanisms an operating system provides to allow processes it manages to share data. Methods for achieving IPC are divided into categories which vary based on software requirements, such as performance and modularity requirements, and system circumstances. Linux inherited from Unix the following IPC mechanisms:
Signals (⚲ API ↪ ⚙️ implementations):
- man 2 kill sends signal to a process
- man 2 tgkill ↪ do_tkill id sends a signal to a thread
- man 2 process_vm_readv ↪ process_vm_rw id - zero-copy data transfer between process address spaces
🔧 TODO: man 2 sigaction man 2 signal man 2 sigaltstack man 2 sigpending man 2 sigprocmask man 2 sigsuspend man 2 sigwaitinfo man 2 sigtimedwait
- Anonymous pipes and named pipes (FIFOs) man 2 mknod ↪ do_mknodat id S_IFIFO id
- Express Data Path PF_XDP id
- Unix Sockets PF_UNIX id
- Memory-mapped files man 2 mmap ⤑ ksys_mmap_pgoff id
- Sys V IPC:
- Message queues
- Semaphores
- Shared memory: man 2 shmget, man 2 shmctl, man 2 shmat, man 2 shmdt
📚 References
Threads or tasks
In Linux kernel "thread" and "task" are almost synonyms.
⚲ API
- linux/sched.h inc - the main scheduler API
- arch/x86/include/asm/current.h src
- current id and get_current id () return current task_struct id
- uapi/linux/taskstats.h inc per-task statistics
- linux/thread_info.h inc
- function current_thread_info id() returns thread_info id
- linux/sched/task.h inc - interface between the scheduler and various task lifetime (fork()/exit()) functionality
- linux/kthread.h inc - simple interface for creating and stopping kernel threads without mess.
- kthread_run id creates and wake a thread
- kthread_create id
⚙️ Internals
Process Scheduling
The process scheduler is the part of the operating system that decides which process runs at a certain point in time. It usually has the ability to pause a running process, move it to the back of the running queue and start a new process.
Active processes are placed in an array called a run queue, or runqueue - rq id. The run queue may contain priority values for each process, which will be used by the scheduler to determine which process to run next. To ensure each program has a fair share of resources, each one is run for some time period (quantum) before it is paused and placed back into the run queue. When a program is stopped to let another run, the program with the highest priority in the run queue is then allowed to execute. Processes are also removed from the run queue when they ask to sleep, are waiting on a resource to become available, or have been terminated.
Linux uses the Completely Fair Scheduler (CFS), the first implementation of a fair queuing process scheduler widely used in a general-purpose operating system. CFS uses a well-studied, classic scheduling algorithm called "fair queuing" originally invented for packet networks. The CFS scheduler has a scheduling complexity of O(log N), where N is the number of tasks in the runqueue. Choosing a task can be done in constant time, but reinserting a task after it has run requires O(log N) operations, because the run queue is implemented as a red–black tree.
In contrast to the previous O(1) scheduler, the CFS scheduler implementation is not based on run queues. Instead, a red-black tree implements a "timeline" of future task execution. Additionally, the scheduler uses nanosecond granularity accounting, the atomic units by which an individual process' share of the CPU was allocated (thus making redundant the previous notion of timeslices). This precise knowledge also means that no specific heuristics are required to determine the interactivity of a process, for example.
Like the old O(1) scheduler, CFS uses a concept called "sleeper fairness", which considers sleeping or waiting tasks equivalent to those on the runqueue. This means that interactive tasks which spend most of their time waiting for user input or other events get a comparable share of CPU time when they need it.
The data structure used for the scheduling algorithm is a red-black tree in which the nodes are scheduler specific structures, entitled sched_entity id. These are derived from the general task_struct process descriptor, with added scheduler elements. These nodes are indexed by processor execution time in nanoseconds. A maximum execution time is also calculated for each process. This time is based upon the idea that an "ideal processor" would equally share processing power amongst all processes. Thus, the maximum execution time is the time the process has been waiting to run, divided by the total number of processes, or in other words, the maximum execution time is the time the process would have expected to run on an "ideal processor".
When the scheduler is invoked to run a new processes, the operation of the scheduler is as follows:
- The left most node of the scheduling tree is chosen (as it will have the lowest spent execution time), and sent for execution.
- If the process simply completes execution, it is removed from the system and scheduling tree.
- If the process reaches its maximum execution time or is otherwise stopped (voluntarily or via interrupt) it is reinserted into the scheduling tree based on its new spent execution time.
- The new left-most node will then be selected from the tree, repeating the iteration.
If the process spends a lot of its time sleeping, then its spent time value is low and it automatically gets the priority boost when it finally needs it. Hence such tasks do not get less processor time than the tasks that are constantly running.
An alternative to CFS is the Brain Fuck Scheduler (BFS) created by Con Kolivas. The objective of BFS, compared to other schedulers, is to provide a scheduler with a simpler algorithm, that does not require adjustment of heuristics or tuning parameters to tailor performance to a specific type of computation workload.
The Linux kernel contains different scheduler classes (or policies). The Completely Fair Scheduler used nowadays by default is SCHED_NORMAL id scheduler class aka SCHED_OTHER. The kernel also contains two additional classes SCHED_BATCH id and SCHED_IDLE id, and another two real-time scheduling classes named SCHED_FIFO id (realtime first-in-first-out) and SCHED_RR id (realtime round-robin), with a third realtime scheduling policy known as SCHED_DEADLINE id that implements the earliest deadline first algorithm (EDF) added later. Any realtime scheduler class takes precedence over any of the "normal" —i.e. non realtime— classes. The scheduler class is selected and configured through the man 2 sched_setscheduler ↪ do_sched_setscheduler id system call.
⚲ API
- linux/sched.h inc - the main scheduler API
⚙️ Internals
- sched_init id is called from start_kernel id
- __schedule id is the main scheduler function.
📚 References
- man 7 sched
- Scheduling doc
- Completely Fair Scheduler doc
- Deadline Task Scheduler doc
- sched ltp
- sched_setparam ltp
- sched_getscheduler ltp
- sched_setscheduler ltp
Wait queues
A wait queue in the kernel is a data structure that allows one or more processes to wait (sleep) until something of interest happens. They are used throughout the kernel to wait for available memory, I/O completion, message arrival, and many other things. In the early days of Linux, a wait queue was a simple list of waiting processes, but various scalability problems (including the thundering herd problem) have led to the addition of a fair amount of complexity since then.
⚲ API:
wait_queue_head id consists of double linked list of wait_queue_entry id and a spinlock.
Waiting for simple events:
- Use one of two methods for wait_queue_head id initialization:
- init_waitqueue_head id initializes wait_queue_head id in function context
- DECLARE_WAIT_QUEUE_HEAD id - actually defines wait_queue_head id in global context
- Wait alternatives:
- wait_event_interruptible id - preferable wait
- wait_event_interruptible_timeout id
- wait_event id - uninterruptible wait. Can cause deadlock ⚠
- wake_up id etc
👁 For example usage see references to unique suspend_queue id.
Explicit use of add_wait_queue instead of simple wait_event for complex cases:
- DECLARE_WAITQUEUE id actually defines wait_queue_entry with default_wake_function id
- add_wait_queue id inserts process in the first position of a wait queue
- remove_wait_queue id
⚙️ Internals:
📚 References:
Synchronization
Thread synchronization is defined as a mechanism which ensures that two or more concurrent processes or threads do not simultaneously execute some particular program segment known as mutual exclusion (mutex). When one thread starts executing the critical section (serialized segment of the program) the other thread should wait until the first thread finishes. If proper synchronization techniques are not applied, it may cause a race condition where, the values of variables may be unpredictable and vary depending on the timings of context switches of the processes or threads.
User space synchronization
Futex
A man 2 futex ↪ do_futex id (short for "fast userspace mutex") is a kernel system call that programmers can use to implement basic locking, or as a building block for higher-level locking abstractions such as semaphores and POSIX mutexes or condition variables.
A futex consists of a kernelspace wait queue that is attached to an aligned integer in userspace. Multiple processes or threads operate on the integer entirely in userspace (using atomic operations to avoid interfering with one another), and only resort to relatively expensive system calls to request operations on the wait queue (for example to wake up waiting processes, or to put the current process on the wait queue). A properly programmed futex-based lock will not use system calls except when the lock is contended; since most operations do not require arbitration between processes, this will not happen in most cases.
The basic operations of futexes are based on only two central operations futex_wait id and futex_wake id though implementation has a more operations for more specialized cases.
- WAIT (addr, val) checks if the value stored at the address addr is val, and if it is puts the current thread to sleep.
- WAKE (addr, val) wakes up val number of threads waiting on the address addr.
⚲ API:
⚙️ Internals: kernel/futex.c src
📚 References
File locking
⚲ API: man 2 flock
Semaphore
💾 History: Semaphore is part of System V IPC man 7 sysvipc
⚲ API:
⚙️ Internals: ipc/sem.c src
Kernel space synchronization
For kernel mode synchronization Linux provides three categories of locking primitives: sleeping, local locks and spinning locks.
1. Sleeping locks:
- mutex id has owner and usage constrains, more easy to debug then semaphore
- rt_mutex id blocking mutual exclusion locks with priority inheritance (PI) support
- semaphore id - use mutex instead semaphore if possible
- ww_mutex id Wound/Wait mutexes: blocking mutual exclusion locks with deadlock avoidance
- rw_semaphore id readers–writer semaphores
- percpu_rw_semaphore id
3. Spinning locks
RW - multiple Readers and single Writer lock mechanism
Enabling and disabling of kernel preemption replaced spinlocks on uniprocessor systems.
💾 History: Prior to kernel version 2.6, Linux disabled interrupt to implement short critical sections. Since version 2.6 and later, Linux is fully preemptive.
⚲ API:
⚙️ Internals:
kernel/locking src
📚 References
Spinlocks
a spinlock is a lock which causes a thread trying to acquire it to simply wait in a loop ("spin") while repeatedly checking if the lock is available. Since the thread remains active but is not performing a useful task, the use of such a lock is a kind of busy waiting. Once acquired, spinlocks will usually be held until they are explicitly released, although in some implementations they may be automatically released if the thread being waited on (that which holds the lock) blocks, or "goes to sleep".
Spinlocks are commonly used inside kernels because they are efficient if threads are likely to be blocked for only short periods. However, spinlocks become wasteful if held for longer durations, as they may prevent other threads from running and require rescheduling. 👁 For example kobj_kset_join id uses spinlock to protect assess to the linked list.
📚 References
- spinlock_t id
- raw_spinlock_t id
- bit_spin_lock id
- Spinlock
- Introduction to spinlocks
- Queued spinlocks
Seqlocks
A seqlock (short for "sequential lock") is a special locking mechanism used in Linux for supporting fast writes of shared variables between two parallel operating system routines. It is a special solution to the readers–writers problem when the number of writers is small.
💾 History: The semantics stabilized as of version 2.5.59, and they are present in the 2.6.x stable kernel series. The seqlocks were developed by Stephen Hemminger and originally called frlocks, based on earlier work by Andrea Arcangeli. The first implementation was in the x86-64 time code where it was needed to synchronize with user space where it was not possible to use a real lock.
It is a reader-writer consistent mechanism which avoids the problem of writer starvation. A seqlock consists of storage for saving a sequence number in addition to a lock. The lock is to support synchronization between two writers and the counter is for indicating consistency in readers. In addition to updating the shared data, the writer increments the sequence number, both after acquiring the lock and before releasing the lock. Readers read the sequence number before and after reading the shared data. If the sequence number is odd on either occasion, a writer had taken the lock while the data was being read and it may have changed. If the sequence numbers are different, a writer has changed the data while it was being read. In either case readers simply retry (using a loop) until they read the same even sequence number before and after.
⚲ API:
📚 References
👁 Example: mount_lock id, defined in fs/namespace.c src
Read-Copy-Update
Another synchronization mechanism that solves the readers–writers problem is the read-copy-update (RCU) algorithm. Read-copy-update implements a kind of mutual exclusion that is wait-free (non-blocking) for readers, allowing extremely low overhead. However, RCU updates can be expensive, as they must leave the old versions of the data structure in place to accommodate pre-existing readers.
RCU was added to Linux in October 2002. Since then, there are thousandths uses of the RCU API within the kernel including the networking protocol stacks and the memory-management system. The implementation of RCU in version 2.6 of the Linux kernel is among the better-known RCU implementations.
The core API is quite small:
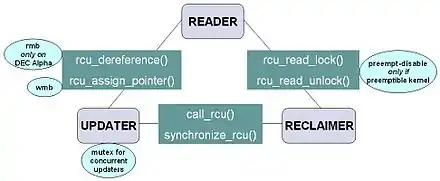
- rcu_read_lock id marks an RCU-protected data structure so that it won't be reclaimed for the full duration of that critical section.
- rcu_read_unlock id is used by a reader to inform the reclaimer that the reader is exiting an RCU read-side critical section. Note that RCU read-side critical sections may be nested and/or overlapping.
- synchronize_rcu id blocks until all pre-existing RCU read-side critical sections on all CPUs have completed. Note that
synchronize_rcuwill not necessarily wait for any subsequent RCU read-side critical sections to complete.
👁 For example, consider the following sequence of events:
CPU 0 CPU 1 CPU 2 ----------------- ------------------------- --------------- 1. rcu_read_lock() 2. enters synchronize_rcu() 3. rcu_read_lock() 4. rcu_read_unlock() 5. exits synchronize_rcu() 6. rcu_read_unlock()
- Since
synchronize_rcuis the API that must figure out when readers are done, its implementation is key to RCU. For RCU to be useful in all but the most read-intensive situations,synchronize_rcu's overhead must also be quite small.
- Alternatively, instead of blocking, synchronize_rcu may register a callback to be invoked after all ongoing RCU read-side critical sections have completed. This callback variant is called call_rcu id in the Linux kernel.
- rcu_assign_pointer id - The updater uses this function to assign a new value to an RCU-protected pointer, in order to safely communicate the change in value from the updater to the reader. This function returns the new value, and also executes any memory barrier instructions required for a given CPU architecture. Perhaps more importantly, it serves to document which pointers are protected by RCU.
- rcu_dereference id - The reader uses this function to fetch an RCU-protected pointer, which returns a value that may then be safely dereferenced. It also executes any directives required by the compiler or the CPU, for example, a volatile cast for gcc, a memory_order_consume load for C/C++11 or the memory-barrier instruction required by the old DEC Alpha CPU. The value returned by
rcu_dereferenceis valid only within the enclosing RCU read-side critical section. As withrcu_assign_pointer, an important function ofrcu_dereferenceis to document which pointers are protected by RCU.
The RCU infrastructure observes the time sequence of rcu_read_lock, rcu_read_unlock, synchronize_rcu, and call_rcu invocations in order to determine when (1) synchronize_rcu invocations may return to their callers and (2) call_rcu callbacks may be invoked. Efficient implementations of the RCU infrastructure make heavy use of batching in order to amortize their overhead over many uses of the corresponding APIs.
⚲ API:
📚 References
Completion
⚲ API:
- completion id - use completion for synchronization task with ISR and task or two tasks.
- wait_for_completion id
- complete id
- linux/completion.h inc
📚 References
📚 References
Interrupts
An interrupt is a signal to the processor emitted by hardware or software indicating an event that needs immediate attention. An interrupt alerts the processor to a high-priority condition requiring the interruption of the current code the processor is executing. The processor responds by suspending its current activities, saving its state, and executing a function called an interrupt handler (or an interrupt service routine, ISR) to deal with the event. This interruption is temporary, and, after the interrupt handler finishes, the processor resumes normal activities.
There are two types of interrupts: hardware interrupts and software interrupts. Hardware interrupts are used by devices to communicate that they require attention from the operating system. For example, pressing a key on the keyboard or moving the mouse triggers hardware interrupts that cause the processor to read the keystroke or mouse position. Unlike the software type, hardware interrupts are asynchronous and can occur in the middle of instruction execution, requiring additional care in programming. The act of initiating a hardware interrupt is referred to as an interrupt request - IRQ (⚙️ do_IRQ id).
A software interrupt is caused either by an exceptional condition in the processor itself, or a special instruction in the instruction set which causes an interrupt when it is executed. The former is often called a trap (⚙️ do_trap id) or exception and is used for errors or events occurring during program execution that are exceptional enough that they cannot be handled within the program itself. For example, if the processor's arithmetic logic unit is commanded to divide a number by zero, this impossible demand will cause a divide-by-zero exception (⚙️ X86_TRAP_DE id), perhaps causing the computer to abandon the calculation or display an error message. Software interrupt instructions function similarly to subroutine calls and are used for a variety of purposes, such as to request services from low-level system software such as device drivers. For example, computers often use software interrupt instructions to communicate with the disk controller to request data be read or written to the disk.
Each interrupt has its own interrupt handler. The number of hardware interrupts is limited by the number of interrupt request (IRQ) lines to the processor, but there may be hundreds of different software interrupts.
⚲ API:
- There are many ways to request ISR, two of them:
- devm_request_threaded_irq id - preferable function to allocate an interrupt line for a managed device with a threaded ISR
- request_irq id, free_irq id - old and common functions to add and remove a handler for an interrupt line
- linux/interrupt.h inc
⚙️ Internals:
📚 References
Deferred works
Scheduler context
Threaded IRQ
⚲ API:
devm_request_threaded_irq id, request_threaded_irq id
ISR should return IRQ_WAKE_THREAD to run thread function
⚙️ Internals:
📚 References
Work
work is a workqueue wrapper
⚲ API: work_struct id, INIT_WORK id, schedule_work id
👁 Example usage samples/ftrace/sample-trace-array.c src
⚙️ Internals: system_wq id
Workqueue
⚲ API:
⚙️ Internals:
Interrupt context
Timer
tasklet is a softirq for periodical tasks
⚲ API
⚙️ Internals:
Tasklet
tasklet is a softirq, for time critical operations
⚲ API is deprecated in favor of threaded IRQs: devm_request_threaded_irq id
⚙️ Internals: tasklet_action_common id HI_SOFTIRQ, TASKLET_SOFTIRQ
Softirq
softirq is internal system facility and should not be used directly. Use tasklet or threaded IRQs
⚲ API
- cat /proc/softirqs
- open_softirq id registers softirq_action id
⚙️ Internals:
⚲ API:
📚 References
CPU specific
Some functions with different implementations for CPU architectures:
- do_boot_cpu id > start_secondary id >cpu_init id
- setup_arch id, start_thread id, get_current id, current id
📚 References